Cybersecurity 101: How Small Businesses Can Protect Their Online Presence
For small businesses, the internet is simultaneously the biggest opportunity and the biggest risk. Your entire operation probably runs on digital tools: website, email, payment processing, customer data, project management. Every one of those touchpoints is a potential entry point for attackers. And they don’t need to be sophisticated. They just need you to be careless once.
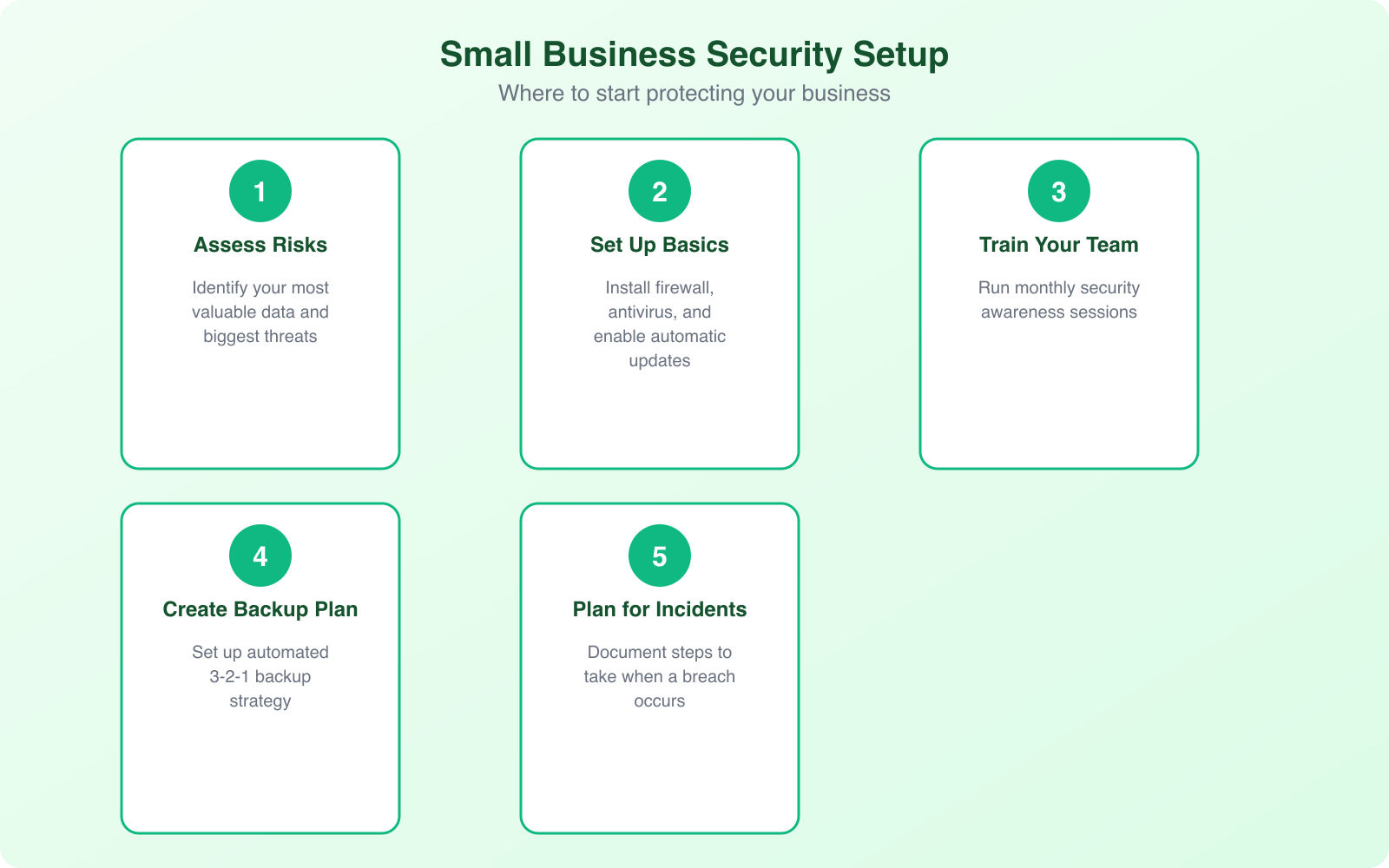
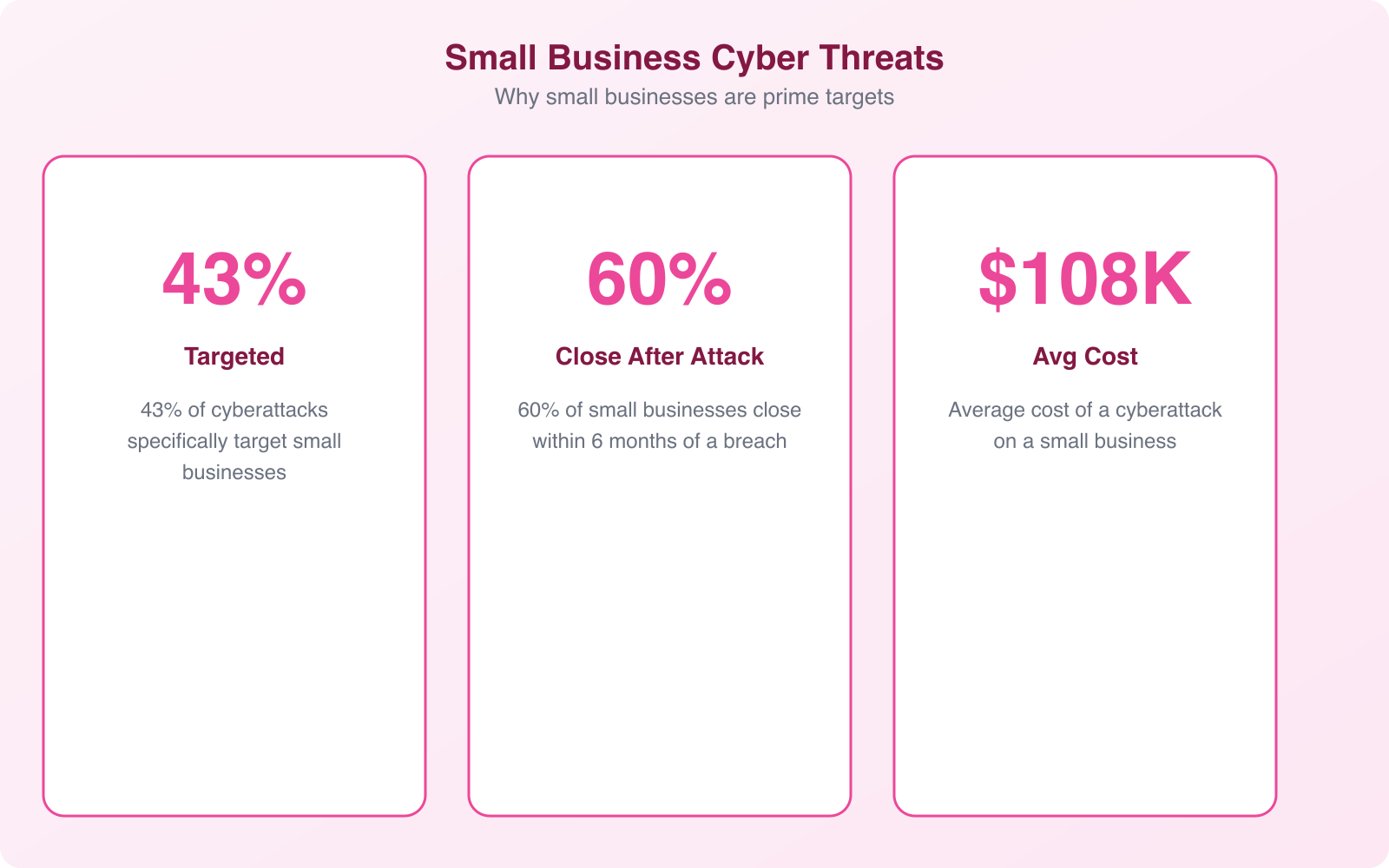
A 2024 industry report revealed that 43% of cyberattacks target small businesses, yet only 14% are prepared to defend themselves. The good news: you don’t need a massive IT budget to protect your business. You need the right habits and a layered approach.
The Small Business Threat Landscape
Small businesses face a specific set of threats that differ from enterprise-level attacks. You’re not getting targeted by state-sponsored hackers (probably). You’re getting hit by automated bots that scan the internet 24/7 looking for low-hanging fruit: unpatched WordPress sites, default admin passwords, unencrypted data transfers, and employees who click phishing links.
The most common attacks against small businesses include:
- Phishing emails: Fake invoices, fake password resets, and fake supplier communications designed to steal credentials.
- Ransomware: Software that encrypts your files and demands payment (usually in cryptocurrency) to unlock them.
- Business email compromise (BEC): Attackers impersonate executives or vendors to trick employees into transferring money or sharing sensitive data.
- Credential stuffing: Automated tools that try username/password combinations leaked from other breaches.
- Website defacement and SEO spam: Hackers inject malicious content into your website, damaging your reputation and search rankings.
Attackers use AI-driven bots to find vulnerable targets automatically. If your business is online, you’re in the scan. The attack won’t care whether you have 3 employees or 300.
First Lines of Defense
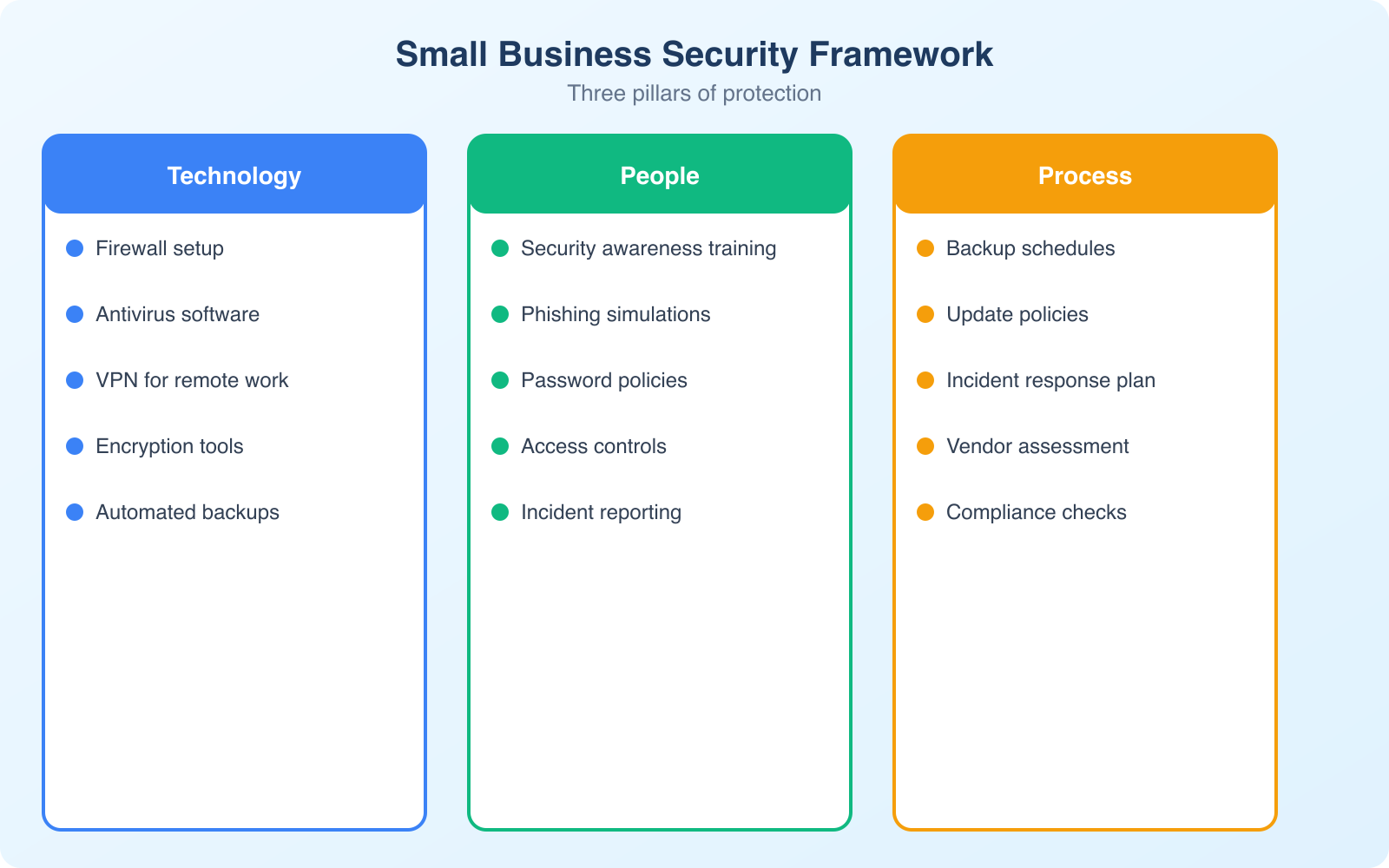
You don’t need an IT department the size of Google’s. But you do need a smart, layered approach. Start with the basics that prevent 80% of attacks:
- Strong, unique passwords for every account. Use a password manager so nobody has to remember them.
- Multi-factor authentication (MFA) on every service that supports it. Email first, then banking, hosting, and business tools.
- Regular software updates for operating systems, browsers, plugins, and all business applications.
- SSL certificates on your website. There’s no excuse for running an unencrypted site.
- Email filtering that catches phishing attempts before they reach inboxes.
When working remotely or handling sensitive files outside your office, a VPN encrypts your internet connection and shields your browsing from anyone on the same network.
The Human Element: Training Your Team
The weakest link in business cybersecurity isn’t always the technology. It’s people. Employees click the wrong link. Owners forget to back up systems. Someone uses “123456” as a password because it’s “easy to remember.”
Training isn’t optional. Teach your staff to:
- Spot suspicious emails by checking sender addresses and hovering over links before clicking
- Verify payment requests through a second channel (call the person who supposedly sent the email)
- Report unusual activity immediately rather than trying to fix it themselves
- Never share passwords, even with coworkers, even temporarily
- Lock screens when stepping away from computers
Make cybersecurity awareness part of your company culture, not an annual memo that everyone ignores. Short monthly briefings of 15-20 minutes covering recent real-world attack examples keep the knowledge fresh and relevant.
Run a quarterly phishing simulation. Send your team a fake phishing email and track who clicks. It sounds aggressive, but it’s the fastest way to identify who needs additional training. The click rate typically drops from 30%+ to under 5% within 3 rounds.
Backup: Your Digital Safety Net
Imagine your office burns down and all paper records are gone. You’d have insurance, right? Your digital operations need the same protection. Regular backups, stored both locally and in the cloud, protect you from ransomware, hardware failures, and accidental deletions.
Automate the backup process. Schedule it so no human has to remember. And test those backups regularly, because a backup that can’t be restored is just a comforting illusion. I recommend testing a full restore at least once per quarter.
For WordPress websites, daily automated backups with at least 30 days of retention give you a safety net against virtually any disaster. Store copies in at least two locations: your hosting environment and an external cloud service like Dropbox or Amazon S3.
Essential Security Tools for Small Businesses
Small businesses can access tools that were once reserved for big corporations. Here’s the minimum toolkit I recommend:
- Web Application Firewall (WAF): Blocks malicious traffic before it reaches your site. Sucuri or Cloudflare are solid options.
- Endpoint protection: Antivirus and anti-malware for all company devices.
- Email security: Spam filters and phishing detection that block threats before they reach inboxes.
- VPN: NordVPN or similar for secure remote access, especially for traveling staff.
- Password manager: Team password sharing without exposing actual credentials. Essential for shared accounts.
The combined cost of these tools is typically $50-$150/month for a small team. Compare that to the average breach cost for small businesses ($120,000-$1.2 million) and the investment is trivial.
Incident Response: When Something Goes Wrong
Even with strong defenses, something might slip through. You need a plan before you need it. An incident response checklist should include:
- Immediate contacts: Who to call internally and externally (IT provider, legal counsel, insurance).
- Containment steps: How to isolate affected systems to prevent the breach from spreading.
- Customer notification process: How and when to inform clients if their data is impacted.
- Law enforcement engagement: When to involve authorities and how to file reports.
- Recovery procedures: How to restore from backups and verify that the threat is eliminated.
Time matters. A breach contained within hours costs far less, both financially and reputationally, than one left unchecked for days. Write the plan now, while you’re calm. You don’t want to be figuring out process during a crisis.
Staying Compliant and Competitive
Depending on your industry, you may be legally required to follow specific data protection rules. GDPR (Europe), CCPA (California), and HIPAA (healthcare) apply even to small operators if you serve certain customers. Fines for non-compliance can cripple a small business faster than the breach itself.
Strong security doesn’t just protect. It sells. Customers are more likely to trust companies that openly demonstrate they care about privacy. A clear “we protect your data” policy, backed by real measures, can be a genuine competitive advantage in 2026.
Building a Security-First Culture
Cybersecurity isn’t something you “finish.” Threats change, tools age, and best practices shift. Review your security posture at least once a year, or more often if your business changes operations, adds staff, or adopts new systems.
You don’t have to outsmart every cybercriminal in the world. You just have to be a harder target than the next business. Criminals, like everyone else, prefer the path of least resistance. Lock your doors, update your locks, and train your team. That alone puts you ahead of 86% of small businesses.
Your online presence is part of your business identity. Guard it as fiercely as your customer list and your brand reputation. With the right habits and a layered approach, small businesses can survive and thrive in this unpredictable digital landscape.
Consider cyber insurance. It’s increasingly affordable for small businesses and can cover breach response costs, legal fees, and customer notification expenses. Think of it as the digital equivalent of property insurance.
Frequently Asked Questions
How much should a small business spend on cybersecurity?
Most small businesses should allocate 5-10% of their IT budget to cybersecurity. For a typical small business, this translates to $50-$300 per month covering WAF, antivirus, VPN, password manager, and backup services. This is a fraction of the average breach cost, which ranges from $120,000 to $1.2 million for small businesses.
What is the biggest cybersecurity threat to small businesses?
Phishing remains the number one threat, accounting for over 36% of all attacks on small businesses. Business email compromise (BEC) is the most financially damaging, often tricking employees into making fraudulent wire transfers. Combined, these social engineering attacks cause more damage than technical exploits because they target human judgment rather than software.
Do I need a dedicated IT person for cybersecurity?
Not necessarily. Many small businesses use managed security service providers (MSSPs) that handle monitoring, updates, and incident response for a monthly fee. This is often more cost-effective than hiring a full-time IT security person. Combined with good employee training and automated tools, an MSSP can cover most small business security needs.
How often should I test my backups?
Test a full restore at least once per quarter. This means actually restoring your backup to a test environment and verifying that everything works: files are intact, databases load correctly, and applications function normally. Many businesses discover their backups are corrupted or incomplete only when they desperately need them. Don’t be one of them.
Is cyber insurance worth it for small businesses?
Yes. Cyber insurance policies for small businesses typically cost $500-$2,000 per year and can cover breach response costs, legal fees, customer notification expenses, and business interruption losses. Given that even a minor breach can cost $120,000+, the insurance premium is a reasonable investment. Look for policies that also include access to incident response teams.